
Revenue
$438.00M
2023
Valuation
$4.30B
2023
Funding
$899.20M
2023
Growth Rate (y/y)
36%
2023
Revenue
Sacra estimates Arctic Wolf hit $438M in annual recurring revenue (ARR) in 2023, up 36% year-over-year, for a 9.8x forward revenue multiple at their $4.3B valuation as of 2021, with over 5,000 customers around the world.
Compare to Palo Alto Networks at $8B ARR, up 15% year-over-year for a 7x multiple at their $56B market cap, and endpoint security platform CrowdStrike at $3.7B ARR, up 33%, for a 27x multiple at their $100B market cap.
Valuation & Funding
Arctic Wolf is valued at $4.43B as of August 2024. Based on 2023 revenue of $438M and their 2023 valuation of $4.30B, the company traded at a 9.8x revenue multiple. The company has raised $879M in total funding. Key investors in the company include Viking Global, Owl Rock, and Blue Owl.
Product
Arctic Wolf was founded in 2012 by Brian NeSmith and Kim Tremblay in Eden Prairie, Minnesota. NeSmith, former CEO of Blue Coat Systems, and Tremblay, former VP of Engineering at Blue Coat, aimed to address the cybersecurity challenges faced by small and mid-sized businesses lacking dedicated security teams.
Their initial vision was to create a "neighborhood watch for IT infrastructure" by aggregating and analyzing data from various security point solutions.
Arctic Wolf found product-market fit with small and mid-sized businesses (50-1000 employees) that lacked dedicated security teams but needed enterprise-grade protection.
Their "SOC-as-a-service" model resonated with IT generalists overwhelmed by managing multiple point solutions. Arctic Wolf's combination of a cloud-native platform and human expertise allowed these companies to outsource 24/7 threat monitoring for $3-8 per user per month. This approach led to 106% year-over-year subscription revenue growth and 301% growth in multi-product customers by 2020.
The core of Arctic Wolf's offering is its Managed Detection and Response (MDR) solution. Key features include:
1. Cloud-native platform that integrates with existing tech stacks
2. 24/7 monitoring of networks, endpoints, and cloud environments
3. AI-powered correlation of events with threat intelligence
4. Dedicated Concierge Security Team for alert triage and threat management
5. Customized security recommendations and guidance
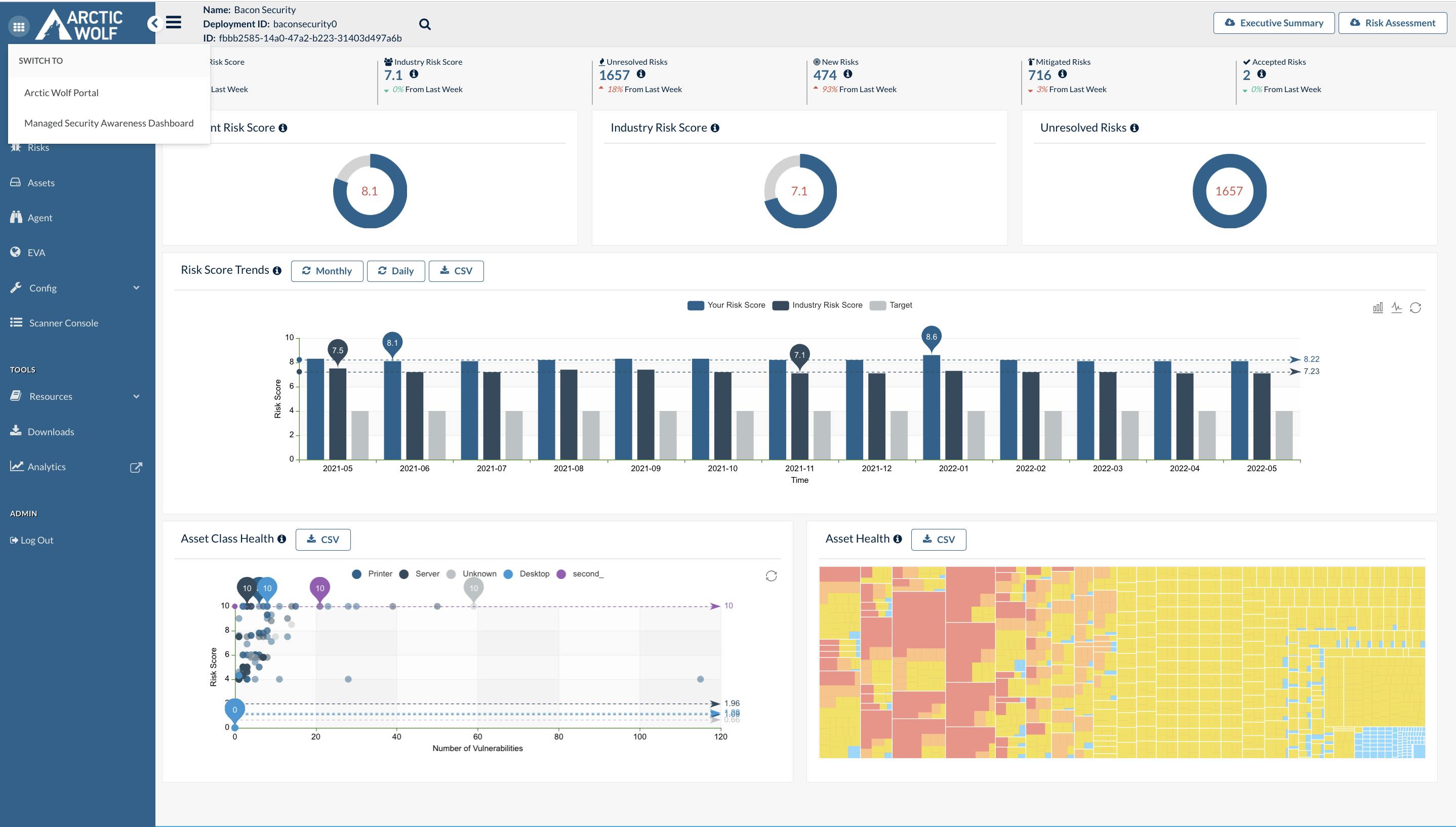
Over time, Arctic Wolf expanded its product suite to include Managed Risk, Cloud Detection and Response, and Managed Security Awareness. The platform processes over 65 billion security events daily across 3,000+ customers. Arctic Wolf's success in the MDR space has positioned it as a leader in the rapidly growing cybersecurity market, with a valuation of $4.3 billion as of 2021.
Business Model
Arctic Wolf is a subscription SaaS company that provides managed detection and response (MDR) services to organizations of all sizes.
The company's core offering is its cloud-native security operations platform, which integrates with a customer's existing tech stack to collect and analyze security events across cloud, network, and endpoint environments.
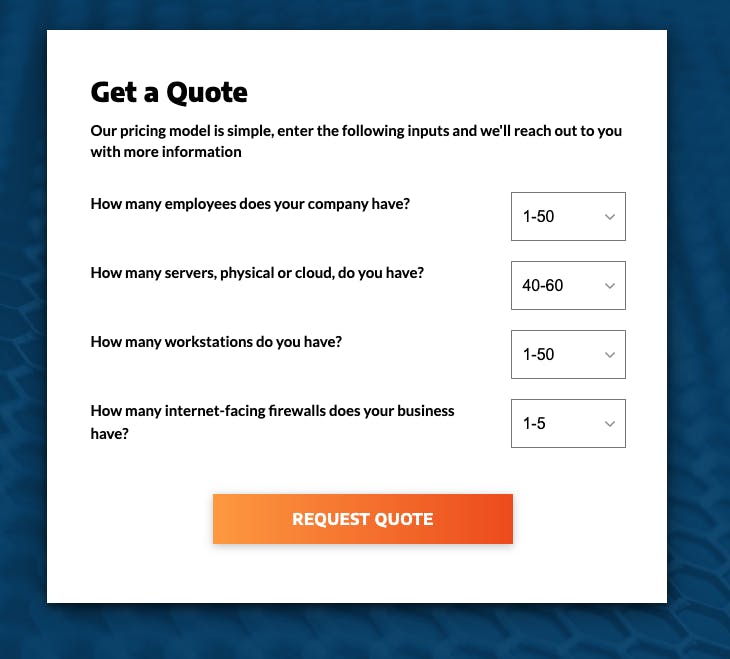
Arctic Wolf's pricing model is based on the number of users and devices a company needs to protect, as well as the specific products and services required.
Arctic Wolf's go-to-market strategy initially focused on small and medium-sized businesses that lacked the resources to build and maintain their own security operations centers.
However, the company has since expanded its target market to include larger enterprises, positioning its offering as a solution to the operational challenges of cybersecurity rather than just a tools or staffing problem.
The company's growth strategy relies heavily on its channel partnerships, with a 100% channel go-to-market approach. This allows Arctic Wolf to efficiently expand its market reach without building a large direct sales force. The company's partner program provides benefits and resources to help partners succeed, fostering a symbiotic relationship that drives mutual growth.
Competition
Arctic Wolf competes in the rapidly growing Managed Detection and Response (MDR) and Extended Detection and Response (XDR) markets, facing competition from both established cybersecurity giants and innovative startups. The competitive landscape can be broadly categorized into three main segments:
Enterprise-Focused MDR/XDR Providers
In this category, Arctic Wolf competes with large, publicly-traded cybersecurity companies like CrowdStrike, Rapid7, and SecureWorks. These competitors offer comprehensive security platforms that include MDR and XDR capabilities, often bundled with other security products.
CrowdStrike, for instance, provides its Falcon platform which combines endpoint protection with MDR services. Arctic Wolf differentiates itself through its cloud-native security operations platform and concierge delivery model, which provides dedicated security experts to each customer. This human-centric approach allows Arctic Wolf to offer more personalized service compared to larger competitors who may rely more heavily on automation.
Mid-Market and SMB-Focused MDR Providers
Here, Arctic Wolf faces competition from companies like eSentire, Red Canary, and Expel. These firms, like Arctic Wolf, often target organizations that lack the resources for a full in-house security operations center. eSentire, for example, offers a similar 24/7 threat detection and response service.
Arctic Wolf stands out in this segment through its modular approach, allowing customers to add capabilities like managed risk assessment and cloud monitoring as needed. The company's recent acquisitions, such as Tetra Defense for incident response, have further expanded its offering to compete more effectively in this space.
Emerging XDR and Security Analytics Platforms
This category includes newer entrants and innovative platforms that are pushing the boundaries of threat detection and response. Companies like SentinelOne, with its Singularity XDR platform, and Hunters.ai, which focuses on autonomous threat hunting, represent this segment.
These competitors often emphasize advanced AI and machine learning capabilities for threat detection. Arctic Wolf counters with its own AI-driven analytics, processing over 1.6 trillion security events weekly according to company statements. However, Arctic Wolf's emphasis on human expertise alongside its technology helps it maintain an edge against purely AI-driven solutions.
TAM Expansion
Arctic Wolf has tailwinds from the growing cybersecurity threat landscape and increasing adoption of managed security services. The company has the opportunity to grow and expand into adjacent markets like cloud security, security awareness training, and incident response.
Managed Detection and Response (MDR) Market Growth
The global MDR market is projected to grow from $2.6 billion in 2022 to $5.6 billion by 2027, at a CAGR of 16.0%. This rapid growth is driven by the increasing sophistication of cyber threats, a shortage of skilled security professionals, and the rising costs of data breaches. As a leader in the MDR space, Arctic Wolf is well-positioned to capture a significant portion of this expanding market.
Arctic Wolf's platform approach, which combines technology with human expertise, addresses the operational challenges many organizations face in managing their security.
By continuing to enhance their core MDR offering and expanding their customer base across different company sizes and industries, Arctic Wolf can ride this market growth wave to substantially increase their revenue and market share.
Cloud Security Expansion
With the accelerating shift to cloud-based infrastructure and applications, cloud security represents a major adjacent market opportunity for Arctic Wolf. The company has already begun expanding in this direction with their Cloud Detection and Response (CDR) and Cloud Security Posture Management (CSPM) solutions.
The global cloud security market is expected to grow from $40.8 billion in 2022 to $77.5 billion by 2026, at a CAGR of 17.3%. By leveraging their existing customer relationships and security operations expertise, Arctic Wolf can develop more comprehensive cloud security offerings.
This could include expanding into areas like Cloud Access Security Broker (CASB) solutions or Zero Trust Network Access (ZTNA), allowing them to capture a larger share of their customers' overall security spend.
Security Awareness and Incident Response
Arctic Wolf has demonstrated their ability to expand into adjacent markets through strategic acquisitions, as evidenced by their purchases of Habitu8 for security awareness training and Tetra Defense for incident response. These moves allow Arctic Wolf to offer a more holistic security solution to their customers.
The security awareness training market is projected to reach $10 billion by 2027, growing at a CAGR of 13%. Meanwhile, the incident response market is expected to hit $68.3 billion by 2028, with a CAGR of 20.5%.
By continuing to invest in and integrate these offerings, Arctic Wolf can increase their average revenue per customer and strengthen their position as a comprehensive security partner for organizations of all sizes.
News
DISCLAIMERS
This report is for information purposes only and is not to be used or considered as an offer or the solicitation of an offer to sell or to buy or subscribe for securities or other financial instruments. Nothing in this report constitutes investment, legal, accounting or tax advice or a representation that any investment or strategy is suitable or appropriate to your individual circumstances or otherwise constitutes a personal trade recommendation to you.
This research report has been prepared solely by Sacra and should not be considered a product of any person or entity that makes such report available, if any.
Information and opinions presented in the sections of the report were obtained or derived from sources Sacra believes are reliable, but Sacra makes no representation as to their accuracy or completeness. Past performance should not be taken as an indication or guarantee of future performance, and no representation or warranty, express or implied, is made regarding future performance. Information, opinions and estimates contained in this report reflect a determination at its original date of publication by Sacra and are subject to change without notice.
Sacra accepts no liability for loss arising from the use of the material presented in this report, except that this exclusion of liability does not apply to the extent that liability arises under specific statutes or regulations applicable to Sacra. Sacra may have issued, and may in the future issue, other reports that are inconsistent with, and reach different conclusions from, the information presented in this report. Those reports reflect different assumptions, views and analytical methods of the analysts who prepared them and Sacra is under no obligation to ensure that such other reports are brought to the attention of any recipient of this report.
All rights reserved. All material presented in this report, unless specifically indicated otherwise is under copyright to Sacra. Sacra reserves any and all intellectual property rights in the report. All trademarks, service marks and logos used in this report are trademarks or service marks or registered trademarks or service marks of Sacra. Any modification, copying, displaying, distributing, transmitting, publishing, licensing, creating derivative works from, or selling any report is strictly prohibited. None of the material, nor its content, nor any copy of it, may be altered in any way, transmitted to, copied or distributed to any other party, without the prior express written permission of Sacra. Any unauthorized duplication, redistribution or disclosure of this report will result in prosecution.